As part of my Node.js development I really wanted to see what was going over the wire from chromium-browser to my Node.js web apps.
I have node.js installed globaly, express installed locally, a very simple express server listening on port 3000
var express = require('express');
var app = express();
app.get('/', function (request, response) {
response.send('Welcome to Express!');
});
app.listen(3000);
Burp Suite setup in my main menu. Added the command via System menu -> Preferences -> Main Menu
The Command string looks like the following.
java -jar -Xmx1024m /WhereTheBurpSuiteLives/burpsuite_free_v1.5.jar
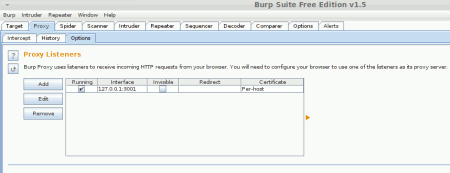
Setting up Burp Suite configuration details are found here. I’ve used Burp Suite before several times. Most notably to create my PowerOffUPSGuests library which I discuss here. In that usage I reverse engineered how the VMware vSphere client shuts down it’s guests and replicated the traffic in my library code. For a simple setup, it’s very easy to use. You can spend hours exploring Burps options and all the devious things you can use it for, but to get started it’s simple. Set it up to listen on localhost and port 3001 for this example.
Run the web app
to start our express app from the directory where our above server is located, from a console, run:
node index.js
Where index.js is the name of the file that contains our JavaScript.
To test that our express server is active. We can browse to http://localhost:3000/ or we can curl it:
curl -i http://localhost:3000/
Should give us something in return like:
HTTP/1.1 200 OK
X-Powered-By: Express
Content-Type: text/html; charset=utf-8
Content-Length: 19
Date: Sun, 24 Mar 2013 07:53:38 GMT
Connection: keep-alive
Welcome to Express!
Now for the Proxy interception (Burp Suite)
Now that we’ve got end to end comms, lets test the interceptor.
Run burpsuite with the command I showed you above.
Fire the Http request at your web app via the proxy:
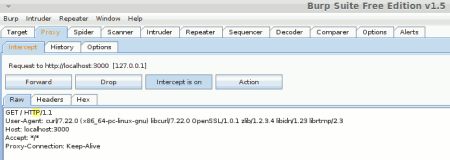
curl -i --proxy http://localhost:3001 http://localhost:3000/
Now you should see burps interceptor catch the request. On the Intercept tab, press the Forward button and curl should show a similar response to above.
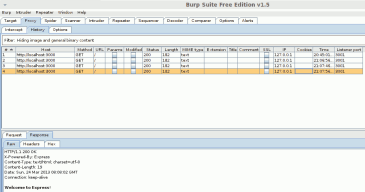
If you look at the History tab, you can select the message curl sent and also see the same Response that curl received.
Now you can also set Burp to intercept the server responses too. In fact Burp is extremely configurable. You can also pass the messages to different components of Burp to process how ever you see fit. As you can see in the above image looking at all the tabs that represent burp tools. These can be very useful for penetration testing your app as you develop it.
I wanted to be able to use chromium normally and also be able to open another window for browsing my express apps and viewing the HTTP via Burp Suite. This is actually quite simple. Again with your app running locally on port 3000 and burp listening on port 3001, run:
chromium-browser --temp-profile --proxy-server=localhost:3001
For more chromium options:
chromium-browser -help
Now you can just browse to your web app and have burp intercept your requests.
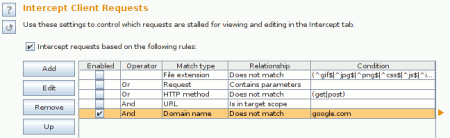
You may also want to ignore requests to your search provider, because as your typing in URL’s chromium will send searches when you pause. Under Proxy->Options tab you can do something like this:
Tags: Http, Http Interception, node, Node.js


Leave a comment